Arsitektur Database Sistem
Tingkat Eksternal (External Level)
Menerangkan view basis data dari sekelompok pemakai.
Tingkat Konseptual (Conseptual Level)
Menerangkan informasi basis data secara me-nyeluruh dengan menyembunyikan penyimpan-an data secara fisik.
Tingkat Internal (Internal Level)
Menerangkan struktur penyimpanan basis data secara fisik dan organisasi file yang digunakan.
Contoh : sebuah file Pegawai yang akan didefinisikan
Tingkat Eksternal (External Level) :
Cobol
01 PEG_REC.
02 PEG_NO PIC X(6).
02 DEPT_NO PIC X(4).
02 GAJI PIC 9(6).
Tingkat Konseptual (Conceptual Level) :
PEGAWAI
NOMOR_PEGAWAI CHARACTER 6
NOMOR_DEPT CHARACTER 4
GAJI NUMERIC 6
Tingkat Internal (Internal Level) :
FILE_PEGAWAI LENGTH = 22
PREFIX TYPE = BYTE (6), OFFSET = 0
EMP# TYPE = BYTE (6), OFFSET = 6,
INDEX = EMPX
DEPT# TYPE = BYTE (4), OFFSET = 12
PAY TYPE = FULLWORD, OFFSET = 16
Data Independence
Kapasitas untuk merubah skema pada satu level sistem basis data tanpa harus merubah skema pada level lainnya.
1.Physical Data Independence
Perubahan pada skema internal dimana tidak mempengaruhi kema konseptual dan eksternal.
2.Logical Data Independence
Perubahan pada skema konseptual dimana tidak mempengaruhi skema eksternal dan aplikasi program.
Mapping (Transformasi)
Proses pendefinisian informasi dari satu level ke level lainnya.
Conceptual/Internal Mapping
Pendefinisian hubungan antara view konseptual dengan basis data di level internal (Bagaimana record-record/field-field didalam level konseptual didefinisikan dilevel internal)
External/Conceptual Mapping
Pendefinisian hubungan antara view konseptual dengan view eksternal
DBMS (Database Management Systems)
DBMS adalah perangkat lunak yang menangani semua pengaksesan database. Mempunyai fasilitas membuat, mangakses, memanipulasi dan memelihara basis data.
Bahasa Dalam DBMS
1.Data Definition Language (DDL)
2.Data Manipulation Language (DML)
Procedural DML
Non Procedural
Fungsi DBMS
1.Data Definition
DBMS harus dapat mengolah pendefinisian data
2.Data Manipulation
DBMS harus dapat menangani permintaan-permintaan dari pemakai untuk mengakses data
3.Data Security & Integrity
DBMS harus dapat memeriksa security dan integrity data yang didefinisikan oleh DBA
4.Data Recovery & Concurency
-DBMS harus dapat menangani kegagalan-kegagalan pengaksesan database yang dapat disebabkan oleh kesalahan sistem, kerusakan disk, dsb.
-DBMS harus dapat mengontrol pengaksesan data yang konkuren yaitu bila satu data diakses secara bersama-sama oleh lebih dari satu pemakai pada saat yang bersamaan.
5.Data Dictionary
DBMS harus menyediakan data dictionary
6.Performance
DBMS harus menangani unjuk kerja dari semua fungsi seefisien mungkin.
Komponen DBMS

1.Query Processsor
2.Database Manager
3.File Manager
4.DML Preprocessor
5.DDL Compiler
6.Dictionary Manager
Arsitektur DBMS Multi User
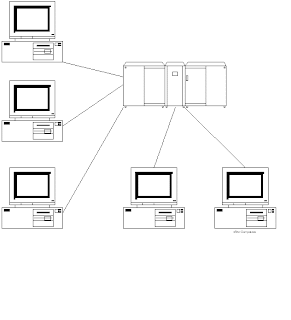
Teleprocessing
Arsitektur tradisional untuk sistem multi user adalah teleprocessing, dimana satu komputer dengan sebuah CPU dan sejumlah terminal seperti pada gambar di bawah ini.
File-Server
Proses didistribusikan ke dalam jaringan, sejenis LAN (Local Area Network). File server mengendalikan file yang diperlukan oleh aplikasi dan DBMS. Meskipun aplikasi dan DBMS dijalankan pada masing-masing workstation, tetapi tetap meminta file dari file server jika diperlukan (perhatikan gambar di bawah ini).

Kerugian arsitektur file-server adalah
-Terdapat lalulintas jaringan yang besar
-Masing-masing workstation membutuhkan copy DBMS
-Kontrol terhadap concurrency, recovery dan integrity menjadi lebih kompleks karena sejumlah DBMS mengakses file secara bersamaan
Client Server
Client-server menunjukkan cara komponen software berinteraksi dalam bentuk sistem.
 Data Dictionary
Data Dictionary Data dictionary adalah tempat penyimpanan informasi yang menggambarkan data dalam database. Data dictionary biasa disebut juga dengan metadata atau data mengenai data.
Berisi tentang :
-nama-nama user yang mempunyai wewenang untuk menggunakan DBMS
-nama-nama item data yang ada dalam database
-jenis dan ukuran item data
-batasan untuk masing-masing item data
Model Data
Sekumpulan konsep-konsep untuk menerangkan data, hubungan-hubungan antara data dan batasan-batasan data yang terintegrasi di dalam suatu organisasi.
1.Model Data Berbasis Objek
Model data berbasis objek menggunakan konsep entitas, atribut dan hubungan antar entitas.
2.Model Data Berbasis Record
Pada model data berbasis record, database terdiri dari sejumlah record dalam bentuk yang tetap yang dapat dibedakan dari bentuknya. Ada 3 macam jenis model data berbasis record, yaitu :
-model data relasional (relational)
-model data hierarkhi (hierarchical)
-model data jaringan (network)
3.Model Data Fisik
Menggambarkan data pada tingkat internal; penyimpanan data secara detailnya dengan format record penyusunan record dan jalur akses.
4.Model Data Konseptual
Menyediakan konsep yang sesuai dengan persepsi pemakai yang memandang datanya.